In today’s digital age, ensuring the security of online accounts and sensitive information is paramount. One effective method to bolster authentication mechanisms is through the implementation of Two-Factor Authentication (2FA), with One-Time Password (OTP) systems being a popular choice. In this blog post, we’ll explore how OTP systems work, the tools and technologies involved, and the necessary steps to integrate them into your applications.
Understanding OTP Systems
OTP systems provide an additional layer of security by requiring users to provide a dynamically generated, one-time password along with their standard credentials (username and password). This ensures that even if an attacker obtains a user’s password, they still need access to the OTP to gain entry, significantly reducing the risk of unauthorized access.
How OTP Works:
- Generation: OTPs are typically generated using cryptographic algorithms and are valid for a short duration, usually 30-60 seconds.
- Delivery: OTPs can be delivered to users via various channels such as SMS, email, mobile apps, or hardware tokens.
- Validation: Upon receiving the OTP, the user enters it along with their username and password. The system verifies the OTP’s validity before granting access.
Tools and Technologies
1. OTP Generation:
- Time-based One-Time Password (TOTP): Uses the current time and a shared secret to generate OTPs. Libraries such as PyOTP (for Python) or java-otp (for Java) can be used.
- HMAC-based One-Time Password (HOTP): Relies on a counter and a shared secret to produce OTPs. Libraries like OTPHP (for PHP) or Otp.NET (for .NET) can be utilized.
2. Delivery:
- SMS Gateways: Services like Twilio, Nexmo, or Plivo can be integrated to send OTPs via SMS.
- Email Services: SMTP services such as SendGrid, Amazon SES, or Gmail’s SMTP can be used to deliver OTPs via email.
- Mobile Apps: Implementing OTP generation within a mobile app using libraries like Google Authenticator or Authy.
3. Validation:
- Server-side Verification: Implement logic on the server to validate the received OTP against the expected OTP using the shared secret.
- Time Synchronization: Ensure the server’s clock is synchronized with the client’s clock to avoid authentication failures due to time discrepancies.
Integration Steps
- Choose OTP Algorithm: Decide whether to use TOTP or HOTP based on your requirements and platform compatibility.
- Select Delivery Channels: Determine which delivery channels (SMS, email, mobile app) best suit your application and user base.
- Implement OTP Generation: Integrate a library or develop functionality to generate OTPs based on the chosen algorithm.
- Set up Delivery Mechanisms: Configure and integrate the selected delivery channels to send OTPs to users.
- Validate OTPs: Implement server-side logic to validate received OTPs against the expected OTPs.
- Handle Expiry and Retry Logic: Define policies for OTP expiry, retry limits, and error handling to enhance security and user experience.
- Test and Monitor: Thoroughly test the OTP system under various scenarios and monitor its performance and effectiveness post-implementation.
Architecture:
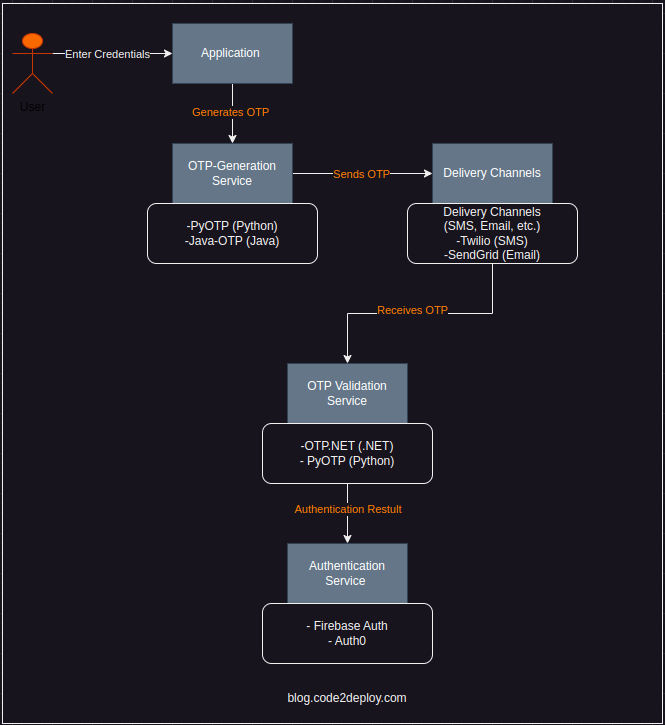
User Interaction:
- User Enters Credentials: The user provides their username and password to initiate the authentication process.
- Application Generates OTP: Upon receiving the user’s credentials, the application generates an OTP using the OTP
- generation service.
- OTP Sent to User: The OTP is delivered to the user via the chosen delivery channel(s), such as SMS or email.
- User Receives OTP: The user receives the OTP and enters it into the application along with their credentials.
- OTP Validation: The application validates the entered OTP using the OTP validation service.
- User Authentication: If the OTP is valid, along with correct credentials, the user is authenticated by the User Authentication service.
- Authentication Result: Based on the authentication result, the user is either granted access to the application or denied access.
Conclusion
Implementing an OTP system adds an additional layer of security to your application, mitigating the risk of unauthorized access and enhancing user confidence. By understanding how OTP systems work and leveraging appropriate tools and technologies, you can effectively integrate 2FA into your applications, safeguarding sensitive information and ensuring a secure user experience.
